TECHNICAL WRITING
MY CLIENT AND BRIEF
This was part of a regular series of technical articles I researched and wrote called "Industry Keywords". Each article would feature a particular technology or service and explain it in easy-to-understand terms.
COPYWRITING AUDIENCE
Over 6,000 technology-literate communications and sales managers around the world who had requested company information and updates.
TECHNICAL WRITING SAMPLE
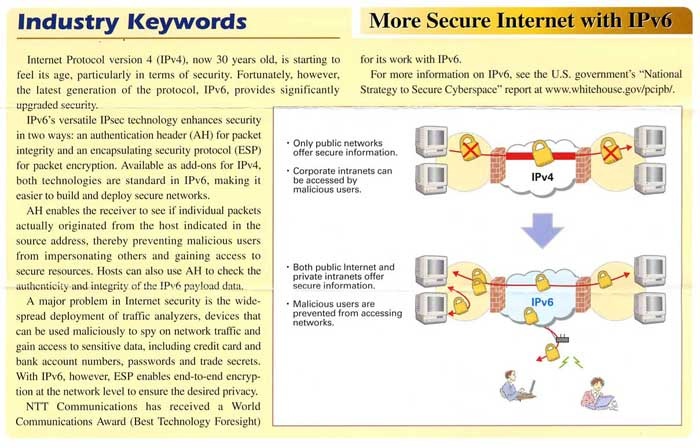
Internet Protocol version 4 (IPv4), now 30 years old, is starting to feel its age, particularly in terms of security. Fortunately, however, the latest generation of the protocol, IPv6, provides significantly upgraded security.
IPv6's versatile Internet Protocol Security ("IPsec") technology enhances security in two ways: an authentication header (AH) for packet integrity and an encapsulating security protocol (ESP) for packet encryption. Available as add-ons for IPv4, both technologies are standard in IPv6, making it easier to build and deploy secure networks.
AH enables the receiver to see if individual packets actually originated from the host indicated in the source address, thereby preventing malicious users from impersonating others and gaining access to secure resources. Hosts can also use AH to check the authenticity and integrity of the IPv6 payload data.
A major problem in Internet security is the widespread deployment of traffic analyzers, devices that can be used maliciously to spy on network traffic and gain access to sensitive data, including credit card and bank account numbers, passwords and trade secrets. With IPv6, however, ESP enables end-to-end encryption at the network level to ensure the desired privacy.
IPv6's versatile Internet Protocol Security ("IPsec") technology enhances security in two ways: an authentication header (AH) for packet integrity and an encapsulating security protocol (ESP) for packet encryption. Available as add-ons for IPv4, both technologies are standard in IPv6, making it easier to build and deploy secure networks.
AH enables the receiver to see if individual packets actually originated from the host indicated in the source address, thereby preventing malicious users from impersonating others and gaining access to secure resources. Hosts can also use AH to check the authenticity and integrity of the IPv6 payload data.
A major problem in Internet security is the widespread deployment of traffic analyzers, devices that can be used maliciously to spy on network traffic and gain access to sensitive data, including credit card and bank account numbers, passwords and trade secrets. With IPv6, however, ESP enables end-to-end encryption at the network level to ensure the desired privacy.